
+359 89 228 1011
Attack Surface Reduced by 35%
Vulnerabilities reduced by 50%
In magna consectetur curabitur tempus diam sagittis non dignissim letius tristique turpis
Our red team simulates real-world attacks to uncover weaknesses before anyone else does.
Your command center for digital defense. Real-time visibility, automation, and control — all in one powerful platform.
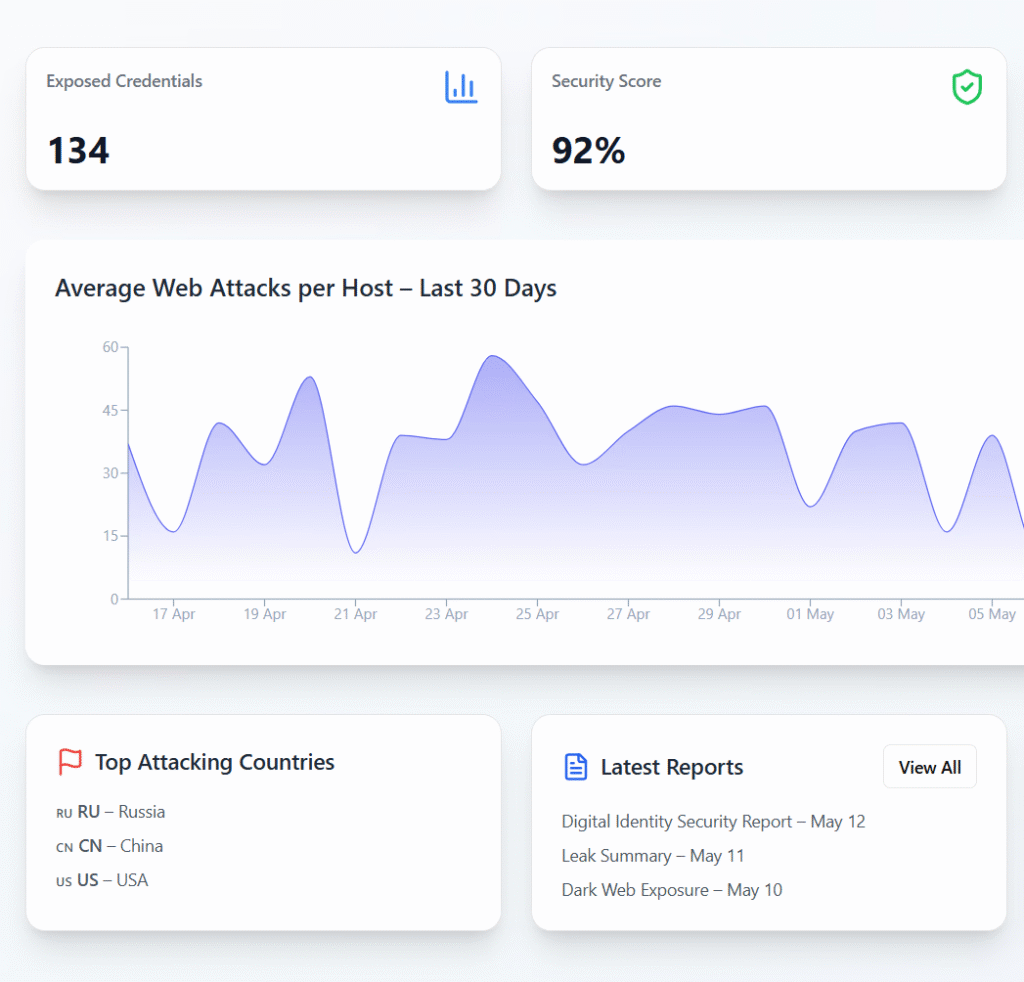
Detect, respond, and adapt to every threat across your entire environment — instantly.
We align your operations with leading global standards — ISO, GDPR, NIS2, and beyond




Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Sherlok LTD specializes in penetration testing, red teaming, and digital identity security. We also develop advanced AppSec and Threat Intelligence solutions, helping organizations detect, analyze, and mitigate cyber threats before they become incidents.
Our clients include startups, SMEs, and enterprise organizations across Europe that require advanced cybersecurity testing, compliance alignment (e.g., GDPR, DORA, ISO 27001), and proactive protection against evolving threats.
Sherlok is built on one belief — cybersecurity should be proactive, not reactive. Our hybrid model of human expertise and AI precision uncovers hidden risks before they turn into threats. Where traditional audits end with a report, Sherlok begins a partnership — guiding you from discovery to measurable resilience.
Simply contact us through our website or email us at [email protected]. We’ll schedule a consultation to understand your needs, outline the testing scope, and provide a detailed proposal — all handled with speed, transparency, and professionalism.
All engagements are conducted under strict confidentiality and NDA agreements. Our testing environments follow ISO/IEC 27001-aligned security protocols, and sensitive data is encrypted both in transit and at rest.
Yes. Every business faces unique threats, so we tailor each engagement to your specific infrastructure, compliance requirements, and risk level. From one-time penetration tests to continuous security monitoring, Sherlok provides scalable solutions to match your goals.